Asymmetric encryption
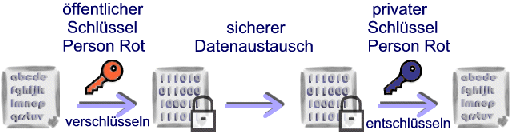 In contrast to symmetric encryption (Sectret Key procedure) with your insecure step of key exchange, asymmetric encryption (Public Key procedure) offers the possibility of secure communication via insecure communication channels (Internet) by using a key pair (private and public key). The generally accessible public key (picture: red) of person A is used to encrypt the file. Afterwards, secure data exchange is also possible via insecure channels such as the Internet, because only person A can decrypt the file with his private (secret) key (picture: blue).
In contrast to symmetric encryption (Sectret Key procedure) with your insecure step of key exchange, asymmetric encryption (Public Key procedure) offers the possibility of secure communication via insecure communication channels (Internet) by using a key pair (private and public key). The generally accessible public key (picture: red) of person A is used to encrypt the file. Afterwards, secure data exchange is also possible via insecure channels such as the Internet, because only person A can decrypt the file with his private (secret) key (picture: blue).
detailed:
Of the encryption methods mentioned above (asymmetric and symmetric), asymmetric encryption (public key method) is always the secure method. The disadvantage is the high mathematical effort and thus the difficulty to encrypt large amounts of data ONLINE. For this reason, a hybrid method is usually used, combining symmetric and asymmetric (public key method) encryption (secret key method). As the name Secret Key implies, the key must not be known to anyone other than you. With the hybrid method, a password (secret key) is first generated with a random generator, which is then used to encrypt the data using a symmetrical encryption method (e.g. 3DES). This can be done relatively quickly. Then only the random password (secret key) with a public key is encrypted according to the asymmetric procedure and attached to the file. Only the recipient who is in possession of the corresponding private key can decrypt the password. Thus he is now able to decrypt the complete data. The advantage of this hybrid procedure is that the password does not have to be transmitted unencrypted via public channels (Internet, telephone) and also changes with each session (encryption). In addition, the high speed of symmetric encryption is combined with the high security and user-friendliness of asymmetric encryption. The private key always belongs together with the public key. We are also talking here about a key pair, both of which are necessary for encryption and decryption according to the asymmetric procedure. Data that has been encrypted with the public key of A can only be decrypted with the private key of A.
Like the password (Secret Key) for symmetric encryption, the private key for asymmetric encryption must not be known to anyone other than the owner (->keep it safe). The advantage of the key pair is that the private key does not have to be transferred, like the password for symmetric encryption. Even if I personally hand over the password (Secret Key) to my partner, there is at least 1 foreign person in possession of the password. For this reason, it is best to define a separate password with each partner using symmetric encryption. This becomes all the more complicated the more passwords you have to remember.
What role does the hash procedure play in this case? - The hash procedure is not an encryption or decryption procedure. According to a mathematically defined mechanism (hash procedure), a kind of "cross sum" is formed over the data. Irrespective of the length of the data (100 bytes, 1000 bytes or 1 MByte), a fixed fingerprint of this data with a fixed length of e.g. 160 bits (RipeMD160) is formed.
If, for example, a hash value is formed via an e-mail and only one character in the e-mail changes, then the hash value also changes. The hash value does not contain large amounts of data and can therefore be encrypted ONLINE with an asymmetric key procedure before transmission. Only the recipient of this e-mail can now restore and check the original hash value with his private key. The recipient can then again create a hash value for their data (e-mail) and compares this with the encrypted hash value. If both values match, then your e-mail or the data was not falsified on the way.
see also: Verschlüsselung Signature Certificate Single Sign-On

 In contrast to symmetric encryption (Sectret Key procedure) with your insecure step of key exchange, asymmetric encryption (Public Key procedure) offers the possibility of secure communication via insecure communication channels (Internet) by using a key pair (private and public key). The generally accessible public key (picture: red) of person A is used to encrypt the file. Afterwards, secure data exchange is also possible via insecure channels such as the Internet, because only person A can decrypt the file with his private (secret) key (picture: blue).
In contrast to symmetric encryption (Sectret Key procedure) with your insecure step of key exchange, asymmetric encryption (Public Key procedure) offers the possibility of secure communication via insecure communication channels (Internet) by using a key pair (private and public key). The generally accessible public key (picture: red) of person A is used to encrypt the file. Afterwards, secure data exchange is also possible via insecure channels such as the Internet, because only person A can decrypt the file with his private (secret) key (picture: blue).