Secret
A secret is required to encrypt data. Only with this secret is it possible to decrypt the data. The abylonsoft software supports the use of X.509 certificates in the HYBRID system and the input of passwords via keyboard in the SYMM system, the use of processor chip cards (e.g. EC cards), the use of memory chip cards (e.g. health insurance cards), written CDs and DVDs, RFID radio cards or USB storage media (e.g. USB sticks).
A good password is at least 12 characters long and contains upper and lower case letters, special characters and numbers. This password should not be used more than once. Additional security is provided by 2-factor authentication, consisting of 2 different secrets. Here a Haqrdwareschlüssel can be combined with a password.
see also: Secret Key Verfahren SYMM-System HYBRID-System Password Authentifizierung Verschlüsseln Zutrittskontrolle

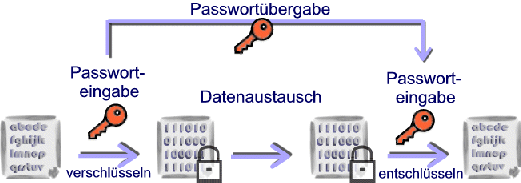 Symmetric encryption has been known since ancient times. The main feature of symmetric encryption is the use of the same key for encryption and decryption, using many different methods (e.g. AES, Blowfish or RC4 algorithms). The individual encryption methods are divided into block encryption and power encryption. The security of the encrypted file depends on the encryption method, the password and the key length. Small key lengths of less than 128 bits are considered insecure today. The higher the key length depending on the encryption algorithm, the more secure is the
Symmetric encryption has been known since ancient times. The main feature of symmetric encryption is the use of the same key for encryption and decryption, using many different methods (e.g. AES, Blowfish or RC4 algorithms). The individual encryption methods are divided into block encryption and power encryption. The security of the encrypted file depends on the encryption method, the password and the key length. Small key lengths of less than 128 bits are considered insecure today. The higher the key length depending on the encryption algorithm, the more secure is the