In this case we can offer the following workarounds.
1. Check plugins
Open the settings dialog and switch to the "Explorer Plugins Settings" page. Check here whether the corresponding PlugIn is activated (check mark).
2. Disable / activate modules
Open the settings dialog and switch to the "Explorer Plugins" page. First deactivate the plugins via the traffic light icon. Then you can activate the plugins again.
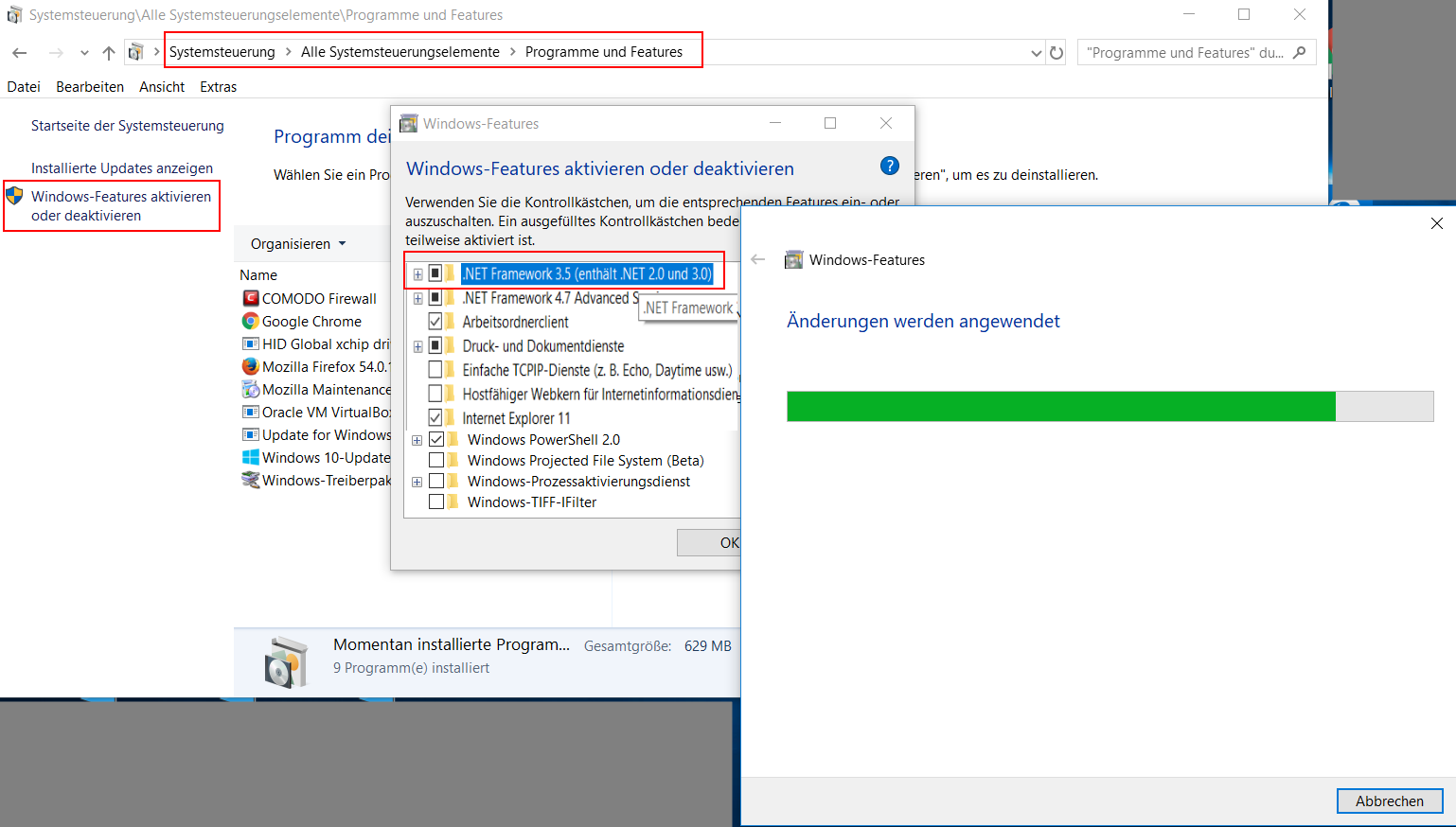
3. Registration of the Plugin-DLL
Start the command line entry with administration rights (Start -> Run -> cmd.exe). Then change to the abylon program directory (with cd). Enter here the command "regsvr32 [Plugin-Dll].
".
As a plugin dll, enter the following files:
- abylon BASIC: 32bit = APMBOle.DLL, 64bit = APMBOleX64.DLL
- abylon READER: 32bit = APMROle.DLL, 64bit = APMROleX64.DLL
- abylon ENTERPRISE: 32bit = APMPOle.DLL, 64bit = APMPOleX64.DLL
- abylon SHREDDER: 32bit = SAWOle.DLL, 64bit = SAWOleX64.DLL
4. Check if all registry entries are present
Open the registry editor (Start -> Run -> regedit.exe) and check if the following 10 entries exist. The menu is only displayed in the File Explorer if all values are present and there are no errors.
1. HKEY_CLASSES_ROOT\*\ShellEx\ContextMenuHandlers\apmcrypt -> REG_SZ: ID see below
2. HKEY_CLASSES_ROOT\CLSID\{ID see below} -> REG_SZ: apmcrypt
3rd HKEY_CLASSES_ROOT\Directory\background\shellex\ContextMenuHandlers\apmcrypt -> REG_SZ: {ID see below}
4. HKEY_CLASSES_ROOT\Directory\shellex\ContextMenuHandlers\apmcrypt -> REG_SZ: {ID see below}
5. HKEY_CLASSES_ROOT\Drive\shellex\ContextMenuHandlers\apmcrypt -> REG_SZ: {ID see below}
6th HKEY_LOCAL_MACHINE\Software\Classes\*\ShellEx\ContextMenuHandlers\apmcrypt -> REG_SZ: {ID see below}
7. HKEY_LOCAL_MACHINE\Software\Classes\CLSID\{ID see below} -> REG_SZ: apmcrypt
8. HKEY_LOCAL_MACHINE\Software\Classes\Directroy\background\shellex\ContextMenuHandlers\apmcrypt -> REG_SZ: {ID see below}
9. HKEY_LOCAL_MACHINE\Software\Classes\Directory\shellex\ContextMenuHandlers\apmcrypt -> REG_SZ: {ID see below}
10th HKEY_LOCAL_MACHINE\Software\Classes\Ddrive\shellex\ContextMenuHandlers\apmcrypt -> REG_SZ: {ID see below}
The following IDs must be used for the individual programs:
- abylon READER = {5fbcd2e0-73dd-11ce-993c-43aa004adb6c}
- abylon BASIC = {5fbcd2e0-73dd-11ce-993c-42aa004adb6c}
- abylon ENTERPRISE = {5fbcd2e0-73dd-11ce-993c-41aa004adb6c}
- abylon SHREDDER = {5fbcd2e0-73dd-11ce-993c-00aa004adb6c}