Credential Provider
The Credential Provider replaces since Windows Vista the GINA (Graphical Identification and Authentication), which is responsible for the secure authentication and logon. In contrast to GINA, the Credential Provider can communicate directly with Winlogon and transfers the collected credentials to it. There are 2 types of Windows Credential Provider:
- Default authentication: Windows logon by password or certificate with a time delay of 120 seconds./li>
- Pre-Logon Access Providers (PLAP): Allows to establish a network connection before logon, without time delay
Thus, for Windows Vista and later, credential providers are the only method for authenticating users. Since the introduction of "Windows Passport" in Windows 10, credential providers can also be used for authentication with apps or websites. In addition, it is an open interface that can be extended by other providers. This is also done by the software abylon LOGON and abylon LOGON Business, which also allows different hardware keys to be used for Windows logon.
The individual credential providers are listed in the registy under HKEY_LOCAL_MACHINE\ SOFTWARE\Microsoft\ Windows\CurrentVersion\ Authentication\Credential Providers. Alternatively, as of Windows 10, these can also be displayed via the editor for local group policies. This is opened via the Run dialog (execute dialog) with gpedit.msc. The entered credential providers are displayed in the tree under Computer Configuration -> Administrative Templates -> System -> Logon (see screenshot).
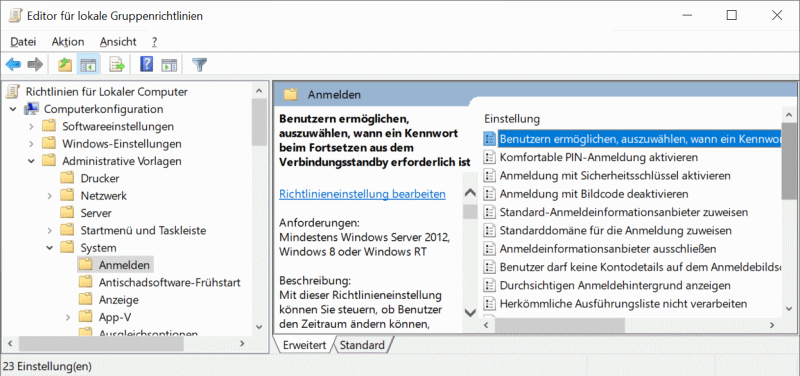
see also: Windows Login Authentication CSP

